Zero Trust Security is a modern-day method to cybersecurity that removes the conventional concept of trusting customers or gadgets within a network. It assumes that no consumer or tool, inner or external, should be depended on via default and requires continuous verification. This version is important in today’s danger landscape wherein attacks can come from …
Introduction to BlackEye Phishing ToolBlackEye is a popular open-source phishing device used for penetration trying out and moral hacking simulations. It presents pre-made phishing templates and lets in ethical hackers to simulate attacks for educational or protection functions. This manual will stroll you thru a way to installation, configure, and use BlackEye for phishing simulations, …
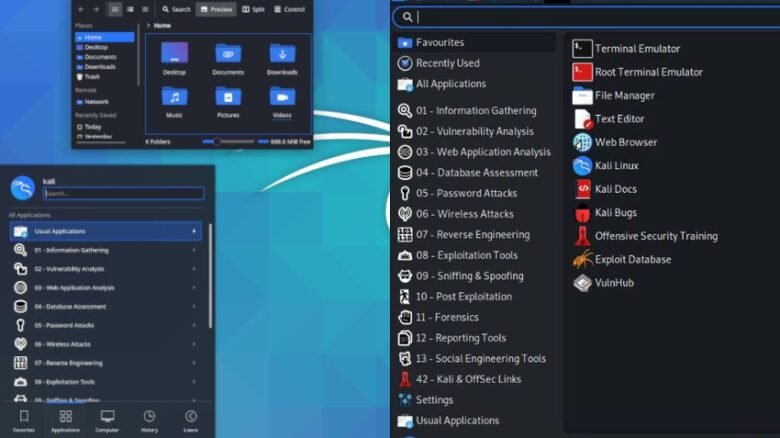
Kali Linux is a powerful open-supply distribution designed for penetration checking out and safety auditing. With a extensive range of integrated equipment, it is a fave amongst cybersecurity specialists and ethical hackers. This guide will walk you through vital Kali Linux gear, supporting you maximize its capability. Steps: Command: This command updates all hooked up …
Welcome to the last aid for gaining knowledge of Wireshark, the sector’s main network protocol analyzer. Whether you’re a community administrator, security professional, or actually an enthusiast looking to recognize how records flows throughout networks, our complete tutorials and gear will assist you examine, seize, and troubleshoot community traffic easily. From knowledge the fundamentals of …
In brand new interconnected digital age, the significance of sturdy cybersecurity can’t be overstated. With the growing frequency and class of cyber threats, protecting your digital global is vital. Whether you’re an individual involved approximately personal information or a business safeguarding sensitive records, professional cybersecurity measures are critical to make sure your digital belongings continue …
Detailed Step-through-Step Guide Introduction to Social Engineering and Social Phishing Types of Social Engineering Attacks How Social Phishing Works Recognizing Social Engineering and Social Phishing Attempts Prevention Strategies and Best Practices Responding to a Social Engineering or Social Phishing Attack Case Studies and Real-World Examples Resources and Further Reading
Guided Exploration with SPDR S&P 500 Expertise Welcome to our comprehensive guide on SPY ETFs and SPDR S&P 500 ETFs. Whether you are a seasoned investor or just beginning your journey inside the world of alternate-traded budget, knowledge the intricacies of SPY and SPDR S&P 500 ETFs is essential for informed choice-making. What is SPY …
Welcome to our complete guide on getting to know Kali Linux NetHunter, the ultimate device for hacking and safety lovers. Whether you are a pro cybersecurity professional or a curious newbie, this manual is designed to equip you with the know-how and skills needed to navigate the sector of ethical hacking and penetration checking out …
Introduction Welcome to our blog post on tricks and tips! In this article, we will be sharing some valuable information to help you enhance your skills and knowledge in various areas. Whether you’re looking for tips on productivity, technology, or personal development, we’ve got you covered. So, let’s dive right in! Productivity Hacks In today’s …
Tricks and Tips for Gathering Information Gathering information is a crucial skill in today’s fast-paced world. Whether you are a student conducting research for a project, a professional looking for industry insights, or simply curious about a particular topic, knowing how to find reliable and relevant information is essential. In this blog post, we will …