Comprehensive Guide to Modern Hacking Tools As cybersecurity threats grow to be greater state-of-the-art, the want for superior gear and techniques to guard towards those threats has in no way been extra. Whether you are…
Zero Trust Security
Zero Trust Security is a modern-day method to cybersecurity that removes the conventional concept of trusting customers or gadgets within a network. It assumes that no consumer or tool, inner or external, should be depended…
BlackEye Phishing Tool | Comprehensive Guide for Phishing…
Introduction to BlackEye Phishing ToolBlackEye is a popular open-source phishing device used for penetration trying out and moral hacking simulations. It presents pre-made phishing templates and lets in ethical hackers to simulate attacks for educational…
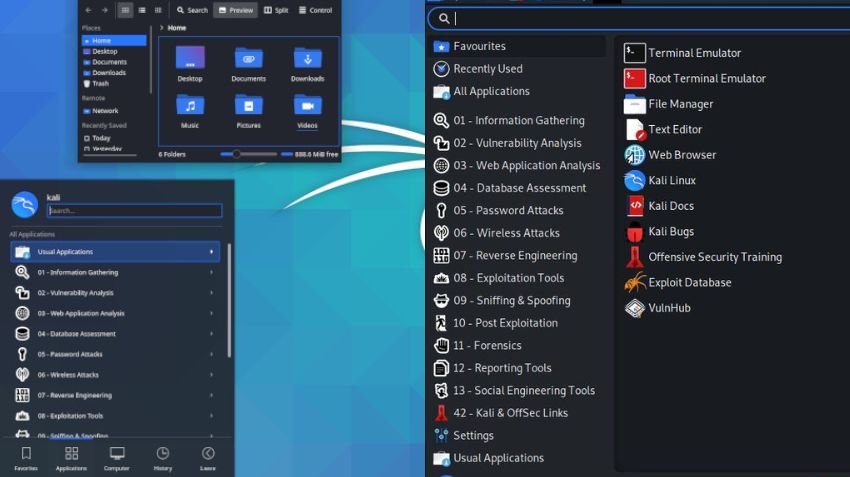
kali linux tools | Essential Security & Penetration…
Kali Linux is a powerful open-supply distribution designed for penetration checking out and safety auditing. With a extensive range of integrated equipment, it is a fave amongst cybersecurity specialists and ethical hackers. This guide will…
Malware and Virus Protection | Real-Time Scanning for…
Malware and Virus Protection nowadays’s virtual landscape, cybersecurity threats like malware, viruses, ransomware, and phishing attacks are continuously evolving. As extra of our non-public, monetary, and professional statistics actions online, it’s essential to have sturdy…
Wireshark Tutorial & Tools | Network Analysis Simplified
Welcome to the last aid for gaining knowledge of Wireshark, the sector’s main network protocol analyzer. Whether you're a community administrator, security professional, or actually an enthusiast looking to recognize how records flows throughout networks,…
best nmap scan for pentest
Best Nmap Scans for Penetration Testing Nmap (Network Mapper) is one of the most powerful and bendy gadget available to cybersecurity professionals and penetration testers. It lets in perceive hosts and services on a network,…
Comprehensive Guide to Hacking LastPass What You Need
hacking lastpass IntroductionIn the ever-evolving world of cybersecurity, password managers like LastPass play a vital function in defensive sensitive information. However, even those gear aren't proof against cyber threats. One of the maximum massive incidents…
Top Hacking Tools and Techniques for Cybersecurity Professionals
Comprehensive Guide to Modern Hacking Tools As cybersecurity threats grow to be greater state-of-the-art, the want for superior gear and techniques to guard towards those threats has in no way been extra. Whether you are…